The importance of safety certification How to implement an effective safety certification method
Digital security has become one of the most critical concerns in modern electronic design. For many engineers, the first thought that comes to mind when discussing security is encryption. However, few consider the importance of security certification, which is actually a fundamental aspect of secure systems. Let’s take an example from the banking sector. When you access your online bank account, you expect your financial data to be encrypted. That’s why you see a small lock icon and “https://†in your browser. This indicates that the website has been authenticated—ensuring it's truly your bank and not a phishing site. If an attacker manages to intercept your login credentials, they could use them to perform unauthorized transactions without your knowledge. To prevent such scenarios, protocols like TLS/SSL are used to ensure both confidentiality and authenticity during internet communications.
Security certification is equally vital in Internet of Things (IoT) applications. Untrusted devices can pose serious risks to an entire network. Consider a smart meter connected to a power grid. An attacker could inject malicious software into the meter, causing it to send false data about energy consumption. This could lead to grid instability or even widespread power outages. To prevent this, it’s essential to verify the authenticity of both the hardware and firmware of these devices. This process is known as secure boot, ensuring only trusted code runs on the device.
Implementing an Effective Security Certification MethodNow that we understand the importance of security certification, let’s explore how to implement it effectively. One of the simplest methods is using a password. In the case of a smart meter, it might send a password to the control system for verification. While easy to implement, this method is vulnerable. Attackers can eavesdrop on the communication, capture the password, and use it to impersonate a legitimate device. Therefore, password-based authentication is generally considered weak and not ideal for secure environments.
A more robust approach is the challenge-response mechanism. There are two main types: symmetric and asymmetric encryption. In symmetric encryption, both the host and the device share a secret key. The host sends a random number (the challenge), and the device uses the key to generate a digital signature. It then sends this back for verification. If the signatures match, the device is authenticated. This ensures the key remains hidden even if the communication is intercepted. Hash functions like SHA-256 are often used because they provide strong mathematical properties that make it nearly impossible to reverse-engineer the key from the output.
Asymmetric encryption, on the other hand, uses a pair of keys: a private key (known only to the device) and a public key (shared with others). The host sends a challenge, and the device signs it using its private key. The host then verifies the signature using the public key. This method is widely used in systems like RSA and ECDSA. It offers stronger security since the private key never needs to be transmitted. This way, the device proves it possesses the private key without revealing it, making the system highly resistant to attacks.
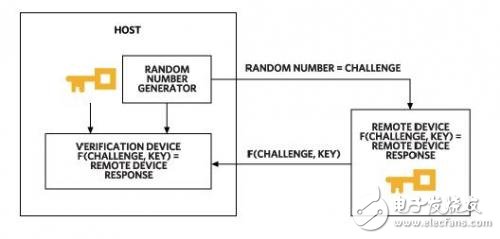
Figure 1. Secure authentication based on symmetric encryption relies on a shared key between the host and the device.
In summary, while passwords may seem simple, they lack the necessary security for critical systems. Challenge-response mechanisms, especially those using asymmetric encryption, offer a much stronger and more reliable way to authenticate devices. Whether in banking, IoT, or any other field, implementing proper security certification is essential to protect against fraud, data breaches, and system compromises. By choosing the right method, developers can build more trustworthy and resilient digital ecosystems.
Shenzhen Priva Tech Co., Ltd. , https://www.privaled.com